

|
|
Initiation responsibility: Head of IT Section, IT Security Management
Implementation responsibility: IT Security Management, Administrators
In addition to the installation and operation of the firewall, other components for the communication between the protected and the external network must be correctly configured. These include, for example, information servers for the provision of information to internal or external users, mail servers and DNS servers.
When configuring the components, a distinction should be made as to whether these are to be set up in the protected network, in the screened sub-net or on the external side of the firewall. To allow a clear distinction to be made, the area between the inner packet filter and the application gateway is referred to as internal screened sub-net, the area between the application gateway and the external packet filter is referred to as external screened sub-net.
External Accesses
Other external accesses to the network requiring protection, e.g. with telnet via a modem pool, should be treated as accesses from the insecure network. This can be achieved, for example, by installing a terminal server with connected modems on the external side of the firewall so that access to the internal computer can only be carried out via Telnet. If virtual private networks (VPNs) are in use, it might be advisable to provide the required access via an additional interface on the application gateway.
Clear regulations must be made so that no external accesses can be created bypassing the firewall. These regulations must be made known to all employees. It must be ensured that both the IT Security Management and the firewall Administrator are informed of relevant plans in good time in order to guarantee inclusion in the IT security concept and the firewall security policy.
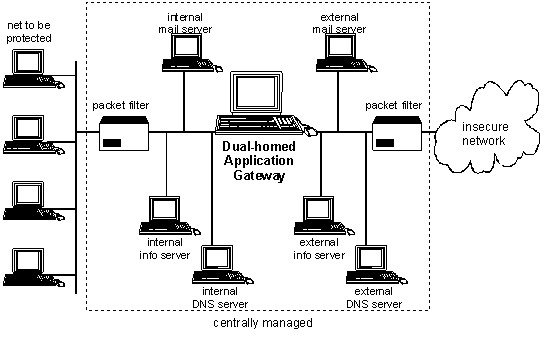
Figure 1: Screened sub-net with dual-homed gateway.
Configuration of information servers
Information servers which provide information to external users must be outside the firewall and be considered in the same way as other servers in the external network. The management of these should either be local or via special time-limited accesses from the protected network. The data should be on write-protected data media.
In the event that some data should only be available for the user of the network to be protected, it is sensible to use further information servers in the internal screened sub-net (see Fig. 1). These data are then not accessible from outside and are protected against internal attacks by the packet filter.
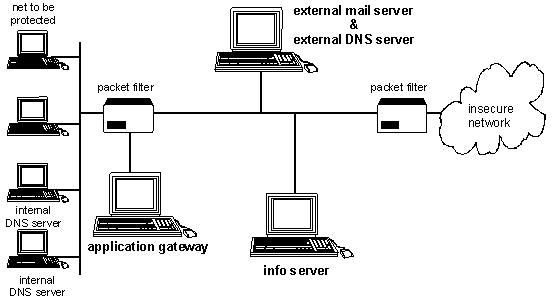
Figure 2: Screened sub-net with application gateway on a separate router interface.
Configuration of the mail servers
A mail server within the protected network is used for the management of the alias data base, which is for the purpose of transforming user addresses to a unified format, for a POP daemon or as a gateway for the connection to another mail system (e.g. X.400). All internal mail is sent to this server and then passed on to the outside via an external mail server.
The external mail server in the external screened sub-net creates the connection with external computers and accepts the mail from here so that the internal structure of the protected network is concealed. This function can be assumed by the application gateway.
This configuration ensures that internal mail cannot enter the external network and a unified address structure can be used..
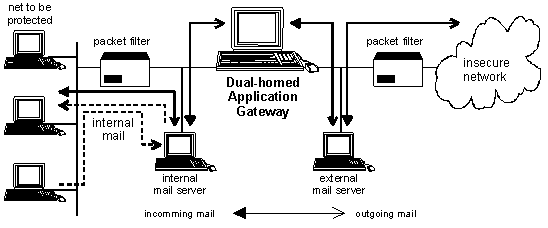
Figure 3: Configuration of the mail servers
Configuration of the DNS servers
Domain Name Service (DNS) is used to convert computer names into IP numbers and vice versa and provides information on computer systems using the network. DNS information should be concealed from the outside world, i.e. Internet or other external networks. The most well-known method of doing this is by a special configuration of two DNS servers (name servers). One DNS server in the internal screened sub-net conceals the structure of the network requiring protection and communicates with a DNS server in the external screened sub-net, in order to transform names of external computers. As DNS clients do not necessarily have to communicate with a DNS server on the same computers, it is possible to have both processes run on different computers.
The external DNS server must be configured in such a way that it claims to be the authority for the domain of the protected network (primary server). Of course, this system only knows what is intended to reach the outside world, i.e. names and IP numbers of external mail servers, the application gateway and the external information server. This is then a public DNS server.
The internal DNS server must also be configured in such a way that it claims to be the authority for the domain of the protected network.. Unlike the external DNS server, this private DNS server manages all internal DNS information and passes on search enquiries from internal computers for external hosts to the external DNS server.
All DNS clients, including those on the application gateway, must be configured in such a way that they always use the internal DNS server (e.g. using entries in the file /etc/resolv.conf).
If an internal client asks for an internal computer, the internal DNS server is used. If an internal client or a client on the application gateway asks for an external computer, the internal DNS server is consulted, which in turn consults the external DNS server, which in turn consults the Internet, which then responds.
An external client which asks for an internal host receives the restricted list from the external DNS server.
The packet filter used must be configured in such a way that only the DNS service is permitted between the servers, i.e. DNS port 53 as the source and destination port. The approval of other ports (> 1023) is thus not necessary.
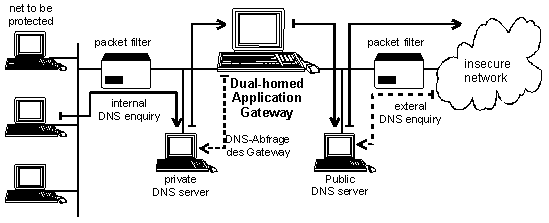
Figure 4: Configuration of the DNS servers
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
July 1999 |