

|
|
 |
8.6 Mobile Telephones
Description
Description
Over the last few years mobile telephones have become an indispensable element of the communications infrastructure. This raises the issue of how they can be used securely.
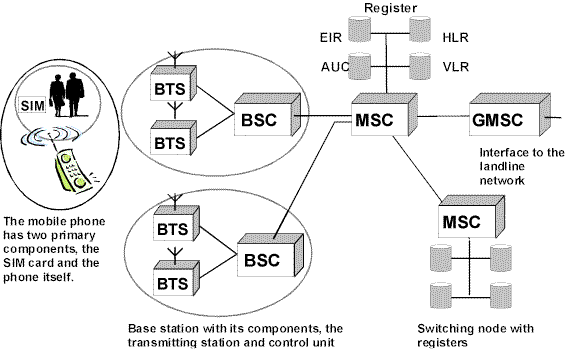
This chapter considers digital mobile telephone systems based on the GSM standard (D and E networks). To ensure that they can be used securely, a number of components and their interaction need to be considered (see diagram):
Mobile telephone
A mobile phone consists of two components, the mobile transceiver itself and the identification module, the Subscriber Identity Module (SIM) card. This enables the GSM network to distinguish between user and mobile terminal.
The mobile transceiver is characterised by its internationally unique serial number or International Mobile Equipment Identity (IMEI). The user is identified by his customer number (International Mobile Subscriber Identity or IMSI), which is stored on the SIM card and is assigned to the subscriber by the network provider at the time that the subscriber enters into a contract with the network provider. This must be distinguished from the telephone number that is assigned to the subscriber (the Mobile Station ISDN Number or MSISDN). This distinction enables a subscriber to use different mobile transceivers with the same SIM card.
The information stored on the SIM card includes the subscriber-specific call number (MSISDN). The cryptographic algorithms for authentication and encryption of user data are also implemented on the SIM card. In addition, short text messages, call charge information and a personal telephone directory can also be stored on the card.
SIM Toolkit
Since 1999, mobile phones and SIM cards with extended menu functionality have been available on the market. This new standard "SIM Toolkit" defines new functions between SIM card and mobile transceiver. As such, it is now possible to download new data and programs provided by the network provider on a regular basis. In this way SIM Toolkit allows some completely new services to be implemented. For example, it provides the card provider with the means to tailor the menu structure of the mobile phone to individual customers' requirements. Thus, if the customer would like to make a hotel reservation or make the travel arrangements for a business trip using his mobile phone, the menu structure of the mobile phone is appropriately modified by the service provider. However, this does require that both the card and also the mobile terminal support the SIM Toolkit standard.
Base station
Every network provider maintains a large number of transmitting stations also called Base Transceiver System (BTS). Each of these stations can cover an area having a radius of between 250m and 35km, depending on the transmitter power and terrain conditions. The coverage area of a transmitting station is referred to as a radio cell. Several radio cells are controlled from one control station or Base Station Controller (BSC). The combination of transmitting stations and control station in turn is referred to as Base Station Subsystem (BSS) or base station for short.
The base station thus constitutes the interface between the network and the mobile phone. It is here that channels for signalling data and user data are made available. The base station is controlled via the Mobile Switching Centre (MSC). This switching node assumes all the technical functions of a landline network switching node, for example, path search, signal path switching and processing of supplementary services. If there is a requirement for a connection to a subscriber in the landline network, this is forwarded by the MSC to the landline network over a switching path (the Gateway Mobile Switching Centre, GMSC).
The encryption of the data on the radio interface, i.e. between mobile phone and base station, can be viewed as a special feature of the GSM network as opposed to the landline network. This should protect the subscriber against unauthorised passive monitoring.
Registers
In order that the network provider is in a position to provide all the services for which demand exists, it must store various items of data. For example, it must know which subscribers are using its network and which services they wish to use. This data, such as the name of the subscriber, his customer number and the services he requires, are stored in the Home Location Register (HLR). If a connection is to be established, for example from a landline network terminal to a mobile phone, the network provider needs to know where the subscriber is and whether his mobile phone is switched on. This information is held in the Visitor Location Register (VLR) and the HLR. To check whether the subscriber is entitled to use the mobile communication network (i.e. he has taken out a card contract), the network provider maintains an identification register at the Authentication Centre (AUC). This holds the security code of the SIM card as well as the PINs determined by the subscriber.
The network provider can also maintain an equipment register, the Equipment Identification Register (EIR), which holds details of all the mobile transceivers permitted on the network broken down into three groups known as the white, grey and black lists. The white list is a register of all the mobile phones which are functioning reliably, the grey list contains all the phones which may possibly be defective, while the black list holds details of all the phones which either have a fault or have been reported stolen. However, not all network providers maintain an equipment register.
In order that the network provider can prepare billing details of the services used by customers, the call data must be stored. This includes, for example, details of communication partners (e.g. call numbers dialled), time and duration of the connection and the location identifiers of the mobile terminals.
Call establishment
As soon as the owner switches on his mobile phone, it registers with the network provider via the nearest base station. The subscriber is identified to the network provider by means of his SIM card and cryptographic algorithms installed on this card. Authentication is effected with the aid of a key which is known only to the network provider and the subscriber. The network provider logs and stores data on the identity of the user, the serial number of the mobile phone and the identity of the base station over which he has registered. This occurs even if no conversation takes place. Moreover, information is stored on every number dialled, irrespective of whether a connection is established. As a result the network provider knows which subscribers are on the network so that connections can now be established from and to subscribers.
Landline network
The conventional public telephone network with its connecting paths is referred to as the landline network.
As every mobile phone connection also entails the use of landline networks, a number of threats relating to the landline network apply also where mobile communication networks are used. The line-connected part of the GSM network is a special instance of an ISDN network. Hence, most of the threats and safeguards which apply to ISDN are applicable to GSM as well. Section 8.4 LAN connection of an IT system via ISDN is therefore also relevant to data transmission over GSM.
This chapter considers those security characteristics of mobile phones which are relevant to persons using them. The intention is to present a systematic approach as to how to draw up a concept for the use of mobile phones within an organisation and ensure that this is implemented and integrated.
Threat Scenario
For IT baseline protection, the following typical threats are assumed to affect the use of mobile phones:
Organisational Shortcomings:
Human Error:
Technical Failures:
Deliberate Acts:
Recommended Countermeasures
To implement IT baseline protection, selection of the required packages of safeguards ("modules") is recommended, as described in Sections 2.3 and 2.4.
In order to be able to use mobile phones securely and effectively, the use of mobile phones should be regulated within the organisation from the outset and security guidelines should be drawn up on the subject (see S 2.188).
The detailed package of safeguards which has been prepared for the use of mobile phones is summarised below.
Organisation:
Hardware and Software:
Communications:
Contingency Planning:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |