

|
|
 |
3.7 Crypto-concept
Description
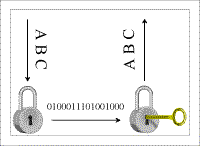
This module describes a process with which, in a heterogeneous environment, both the data stored locally and the data to be transmitted can be protected effectively through cryptographic procedures and techniques. For this purpose, the module explains how and where in a heterogeneous environment cryptographic procedures and the corresponding components can be used. As a large number of influencing factors should be taken into account when using cryptographic procedures, a crypto-concept should be created.
This module describes how to create a crypto-concept. It starts by determining the requirements and influencing factors, then goes on to the selection of suitable cryptographic solutions and products, and ends with raising the awareness of and training the users as well as crypto contingency planning.
This module can also be consulted when only a cryptographic product is to be selected for one of the possible areas of use. In this case, it is possible to leave out several of the steps described in the following and only perform those that are relevant for the particular area of use.
In order to implement this module, it is necessary to have a basic understanding of the fundamental cryptographic mechanisms. An overview of basic cryptographic terms can be found in S 3.23 Introduction to basic cryptographic terms.
Threat Scenario
Cryptographic procedures are used to guarantee
Therefore, the following threats to cryptographic procedures are primarily taken into account for IT baseline protection:
If cryptographic procedures are used, the following threats should also be taken into account for IT baseline protection:
Organisational Shortcomings:
Human Failure:
Technical Failure:
Deliberate Acts:
Recommended Countermeasures (S)
For the implementation of IT baseline protection, selection of the required packages of safeguards ("modules"), as described in chapters 2.3 and 2.4, is recommended. For cryptographic procedures essentially the following additional steps have to be taken:
1. Develop a crypto-concept (see S 2.161)
The use of cryptographic procedures is determined by a large number of influencing factors. These factors include the IT system, the volume of data, the desired level of protectionn and the demands on availability. For this reason, a concept should first be developed which takes into account all influencing factors and criteria which determine the choice of a particular cryptographic procedure and the corresponding products. At the same time, this concept should be economically feasible.
2. Determine the requirements that the cryptographic procedure has to meet
A requirement catalogue must be created which describes the influencing variables and the decision criteria on which the use of cryptographic procedures are based (see S 2.162 Determining the need to use cryptographic procedures and products and S 2.163 Determining the factors influencing cryptographic procedures and products). Cryptographic procedures can be used on the various layers of the ISO/OSI model. According to the specified demands or threats, it is recommended to use the procedure on particular layers (see also S 4.90 Use of cryptographic procedures on the various layers of the ISO/OSI reference model).
3. Select a suitable cryptographic procedure (S 2.164 Selection of a suitable cryptographic procedure)
When selecting cryptographic procedures, it is first necessary to ascertain whether symmetric, asymmetric or hybrid algorithms are suitable then determine the required strength of the mechanism. Finally, suitable products should be determined.
4. Select a suitable cryptographic product (S 2.165 Selection of a suitable cryptographic product)
After all the conditions have been determined, a product must be selected which provides the level of security laid down in the crypto-concept. Such a product, called crypto module for short, can consist of hardware, software, firmware or a combination of these, and of the components such as memory, processors, busses, electricity supply, etc. which are necessary to perform cryptographic processes. A crypto module can be used to protect sensitive data or information in various computer or telecommunications systems.
5. Use the crypto module appropriately (S 2.166 Provisions governing the use of crypto modules)
Even while a crypto module is in operation, it must satisfy a number of security requirements. In addition to ensuring the security of the data that the crypto module is to protect, it is also important to protect the crypto module against direct perpetration and unauthorised interference.
6. The security demands on the IT systems in which the cryptographic procedures are used are to be found in the corresponding system-specific components. For example, the components for clients (including laptops) are to be found in chapter 5 and those for servers in chapter 6.
7. Contingency planning includes
The following describes the safeguards for the area "crypto-concept". Safeguards from other chapters will not be repeated here.
Organisation:
Personnel:
Hardware/Software:
Contingency Planning:
Many other components contain safeguards which touch upon the topic of cryptographic procedures and can be considered as implementation examples. For example, these include:
| © Copyright
by Bundesamt für Sicherheit in der Informationstechnik |
last update: July 1999 |