UnauthorizedModems_6
Protecting Data Networks by Securing Telephone Networks
5
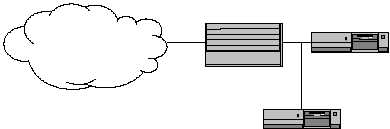
A common tool used in the detection and response portion of the operational
model is an intrusion detection system (IDS). An IDS is designed to sit between
an organization’s firewall and the Internet and observe all traffic intended for the
internal network. It accomplishes this in a passive mode – simply listening to the
traffic without making any attempt to block, reroute, or modify it. It generally
sits on the outside of the firewall (on the Internet side) so it can observe all
traffic intended for the internal network, not just the traffic the firewall allows to
pass through. An IDS will look for connections and traffic it considers
“suspicious” and, should it observe any, will take appropriate actions. The
actions it takes may range from generating an alert message for a system or
security administrator to actually terminating the connection. Suspicious
behavior might include actions such as attempted logins to special accounts,
attempts to take advantage of known security holes, or anything that falls
outside the scope of normal user behavior for that system or network as defined
by the organization’s security policy. Typical intrusion detection system
placement is depicted in Figure 2.
Figure 2. Typical Placement of an Intrusion Detection System
The question that must be asked is whether these security precautions are
enough. In a study conducted in 1997, Zona Research likened the current
security practices of corporations to the Maginot Line. [7] The Maginot Line
was built by France after World War I to defend against a future attack by
Germany. When World War II occurred, however, the German assault was not
stopped by this series of defenses because the French had built them to address
the threats posed by Germany at the conclusion of World War I. The line of
defenses did not address the threats a new, differently configured German army
posed as they simply bypassed the French defenses and entered France via
Belgium. So what threat is it Zona Research is referring to that is not being
addressed by current corporate security practices? What Maginot Line exists in
our corporate networks? Peter Shipley, a computer security consultant in
Berkeley, California, described the problem when he stated:
Companies are investing heavy amounts of money into firewalls and
completely forgetting internal security. It is very common for people to
place fax modems on their desktops, and inadvertently have inbound
dial-in [enabled]. [5]
Firewall
Router
Intrusion Detection System
The Internet