UnauthorizedModems_5
Protecting Data Networks by Securing Telephone Networks
4
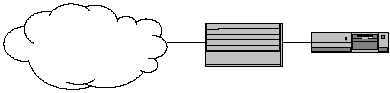
Figure 1. Typical Placement of a Firewall
Since a firewall is actually placed between the internal network and the Internet,
it can be used to filter both incoming and outgoing traffic. Restricting the type of
incoming traffic is done to limit availability of internal services to the outside
world. The firewall, for example, can be set to allow web traffic but to block
remote login connections. In a similar manner traffic exiting the internal
network can also be filtered to help enforce local security or corporate policies.
There might, for example, be an internal policy forbidding access to certain web
sites, or certain sites during specific portions of the day.
With all of these methods to prevent security breaches it might seem computer
and network security should be a simple matter. Unfortunately, it is not. One
factor that complicates the situation is the natural desire of organizations to
connect to the Internet. In order to conduct business in today’s highly
competitive world it is essential for corporations to be connected to the Internet.
This results in a connection which can also potentially be exploited by
unauthorized individuals bent on intruding into computer systems and networks.
The security mechanisms mentioned should, in theory, protect the internal
network from potential intruders and they would were it not for two problems.
The first is the human element that cannot be separated from security. Systems
are configured incorrectly, users don’t follow proper security practices and
procedures, and software is not properly maintained and updated. The second
problem is the fact mistakes are frequently made in the development of software
which will occasionally result in a hole in the security of a system. The
“hacking” community is especially adept at exploiting these holes when they are
discovered and in also passing the information along so others can take
advantage of them as well. System and security administrators, on the other
hand, generally have other duties to perform and often do not hear about a hole
until well after the “hacking” community knows about and has taken advantage
of it. This means despite an organization’s best efforts to secure its network and
computer systems, intrusions may still occasionally occur. This is where the
remaining portion of the operational model comes into play. Prevention is the
goal in security, but when that fails it is essential that penetrations are quickly
detected and an appropriate response taken.
The Internet
Firewall
Internal Network
Router