UnauthorizedModems_14
Protecting Data Networks by Securing Telephone Networks
13
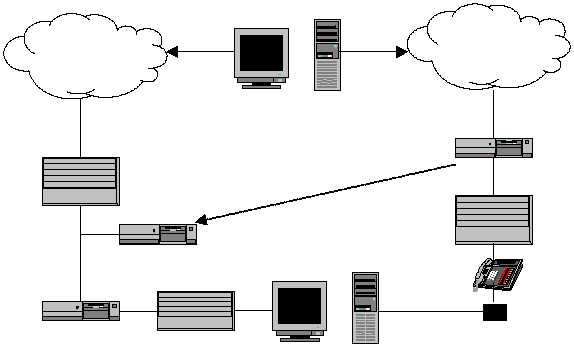
A final basic function desirable in the security device is the ability to integrate
all functions into a single integrated package (as also depicted in Figure 6). This
means more than just placing the functions in the same hardware box. It requires
all aspects be designed such that they interface with each other and provide a
unified package for the security administrator. The security device could, for
example, detect fax or modem usage on a line and after logging the use, perform
a vulnerability check on the fax or modem. The administrator can then notify the
user of the incorrectly configured device so it may be secured or removed if it is
unauthorized. A logging feature is also desirable to provide the administrator
with concise reports detailing the number and type of the various data
communication devices it knows of, the security status of those devices, a record
of the attempts to perform unauthorized transmissions via the devices, and a log
of all calls made along with their type.
Figure 6. Combined Telephone Firewall and Intrusion Detection System
Computer security has traditionally been considered a cost-center. The value it
provides is the often intangible protection of the information stored on the
systems protected. The potential loss as a result of information being obtained
by adversaries, whether government or industry, is tremendous. Consequently,
the cost of applying security measures has been grudgingly accepted but
organizations have always attempted to minimize the expense. Protecting an
organization’s information is an important function. For security to be viewed as
something besides a necessary cost that must be borne, it has to show a return on
the investment. Traditional products, designed to address only the prevention
portion of the operational model, will never show a formal return on the
investment. Although extremely important, they will never provide a savings to
the organization, they just prevent loss. The technology required to address the
detection and response aspects of the operational model as it relates to
telecommunications security, however, can actually result in a savings to an
organization and thus a return on the investment. This is possible because the
Security As A Return
On Investment
Hub
The Internet
Firewall
Router
Intrusion Detection System
End Users
Attacker
Public Telephone
Network
PBX
Modem
Telephone Firewall &
Intrusion Detection System