UnauthorizedModems_13
Protecting Data Networks by Securing Telephone Networks
12
If all the war dialer does is identify which telephone lines are connected to
modems or fax machines, then it could be eliminated by the introduction of the
telephone firewall. If, on the other hand, the software that performs the war
dialing function is more extensive and can attempt to automatically gain
unauthorized access to the systems it detects, then the software is providing
additional useful functionality. A particularly useful feature would be to have
the software utilize more than just simple userid/password combinations and
exploit known holes as well.
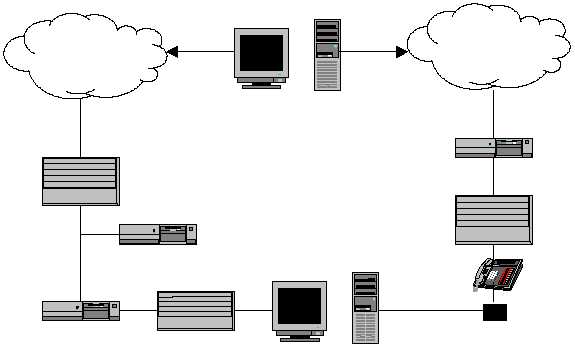
Figure 5. Placement of a Telephone Firewall
A second basic function desirable in a device designed to secure telephone lines
is the ability to perform real-time detection of intrusive activity. This is in
essence a telephone intrusion detection system. Figure 6 shows the
placement of the telephone IDS together with the telephone firewall. The key to
this device is it’s ability to monitor the telephone system and to alert a security
administrator when an unauthorized act occurs. The administrator can then take
the appropriate action whether that is deemed to be termination, monitoring, or
redirection of the connection. Another way to perform telephone intrusion
detection is to incorporate current intrusion detection systems by adding sensors
in the telephone network which would direct activity data to the intrusion
detection system.
Firewall
Hub
End Users
Modem
Router
Intrusion Detection System
The Internet
Attacker
Public Telephone
Network
PBX
Telephone
Firewall