UnauthorizedModems_10
Protecting Data Networks by Securing Telephone Networks
9
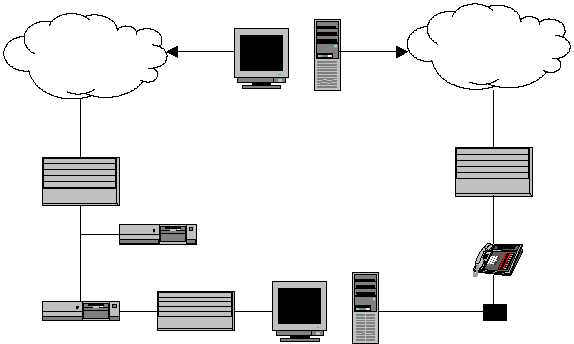
Figure 4. The Actual Corporate Network
Another benefit of firewalls is the fact they provide a convenient chokepoint to
restrict and monitor access to the Internet. A common analogy is to compare
data transmission to a pipe through which water flows. Network connections to
a firewall of the sort depicted in Figure 4, are large pipes through which
tremendous volumes of water (data) flow. Modems, on the other hand, provide
many new access points to the network with no comparable chokepoint from
which to monitor or restrict them. Each of these access points is much smaller –
a minor pipe through which lesser amounts of data may flow but with many
more of these smaller pipes available.
As depicted in Figure 4, the Public Telephone Network, accessible through a
simple modem, poses a tremendous security risk to corporations and
government agencies. The potential security risks include:
·
Unauthorized external access to internal networks or computer systems
·
Unauthorized internal access to external networks or computer systems
·
Loss of software configuration control
The most obvious of these potential security risks is the possible access by
outsiders to a corporation’s internal network. A firewall may be in place to block
access from the Internet but the presence of a modem completely bypasses this
valuable security safeguard. With a “rogue” modem, a hole has effectively been
placed in the security perimeter that had been designed to surround the internal
network. The second risk with modem use is associated with authorized users
performing unauthorized activities from the internal network. This is especially
of concern in high-security environments where any outside transmission is
carefully monitored to ensure corporate or government secrets are not
inadvertently or deliberately transmitted. Related to this problem is the issue of
The Security Issues
Firewall
Intrusion Detection System
Hub
End Users
The Internet
Router
Attacker
Public Telephone
Network
PBX
Modem