ICMP_Scanning_5
ICMP Usage in Scanning
5
Copyright Ó Ofir Arkin, 2000
http://www.sys-security.com
2.0 Host Detection using the ICMP Protocol
The Host Detection stage gives a malicious computer attacker crucial information by identifying
the computers on the targeted network that are reachable from the Internet. This process belongs
to the scanning stage, which is one of the first stages in the Information Gathering process. The
information collected during this stage could later lead to an attempt to break in to one (or more)
of the targeted network computers. This, if the information gathered would be sufficient for the
malicious computer attacker.
2.1 ICMP ECHO (Type 8) and ECHO Reply (Type 0)
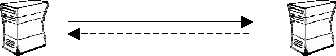
We can use an ICMP ECHO datagram to determine whether a target IP address is active or not,
by simply sending an ICMP ECHO3 (ICMP type 8) datagram to the targeted system and waiting
to see if an ICMP ECHO Reply (ICMP type 0) is received. If an ICMP ECHO reply is received, it
means that the target is alive (few firewalls spoof ICMP ECHO replies from protected hosts); No
response means the target is down or a filtering device is preventing the incoming ICMP ECHO
packet from getting inside the protected network or the filtering device prevents the initiated reply
from reaching the Internet.
Figure 1: ICMP ECHO Mechanism
This mechanism is used by the Ping command to determine if a destination host is reachable.
In the next example two LINUX machines demonstrate the usage of Ping:
[root@stan /root]# ping 192.168.5.5
PING 192.168.5.5 (192.168.5.5) from 192.168.5.1 : 56(84) bytes of data.
64 bytes from 192.168.5.5: icmp_seq=0 ttl=255 time=4.4 ms
64 bytes from 192.168.5.5: icmp_seq=1 ttl=255 time=5.9 ms
64 bytes from 192.168.5.5: icmp_seq=2 ttl=255 time=5.8 ms
--- 192.168.5.5 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 4.4/5.3/5.9 ms
A Snort trace4:
01/26-13:16:25.746316 192.168.5.1 -> 192.168.5.5
ICMP TTL:64 TOS:0x0 ID:6059
3
From a Technical point of view: The sending side initializes the identifier (used to identify ECHO requests aimed at
different destination hosts) and sequence number (if multiple ECHO requests are sent to the same destination host), adds
some data (arbitrary) to the data field and sends the ICMP ECHO to the destination host. In the ICMP header the code
equals zero. The recipient should only change the type to ECHO Reply and return the datagram to the sender.
4
Snort, written by Martin Roesch, can be found at http://www.clark.net/~roesch/security.html.
ICMP ECHO request
If alive and not filtered – ICMP ECHO
Reply