ICMP_Scanning_36
ICMP Usage in Scanning
36
Copyright Ó Ofir Arkin, 2000
http://www.sys-security.com
7.3 Other Considerations
If you want to maintain strong ICMP filtering rules with your Firewall/Filtering-Device I suggest
you block all incoming ICMP traffic except for Type 3 Code 4, which is used by the Path MTU
Discovery process27.
If you will block incoming ICMP “Fragmentation Needed and Don’t Fragment Bit was Set” your
network performance will suffer from degradation. You should understand the security risks
involving in opening this kind of traffic to your protected network. The possibility of a DOS,
Inverse Mapping, Host Detection, and a one-way Covert communication channel (which was not
been seen in the wild yet).
Another consideration could be the usage of network troubleshooting tools such as traceroute
and ping. In the case of traceroute if the filtering device you are using does not support Stateful
inspection with ICMP than allowing ICMP TTL Exceeded In Transit (Type 11, code 0) error
messages inside the protected network could lead to various security hazards. The same goes
with ping, where ICMP ECHO reply is even more dangerous when allowed inside the protected
network (Inverse Mapping, Covert Channel and more security risks).
You can limit the number of systems that really need to use the network troubleshooting tools
with ACL, but bear in mind that those systems could be mapped from the Internet – and this is
only the tip of the iceberg.
27
See Appendix B: “Fragmentation Needed but the Don’t Fragment Bit was set” and the Path MTU Discovery Process.
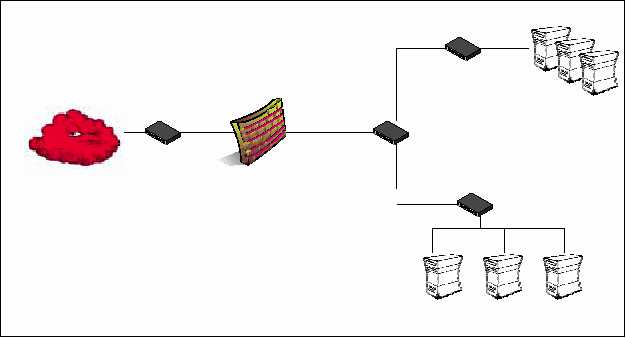
Incoming ICMP Traffic
Type 3 Code 4 – for Path MTU
Discovery process.
DMZ
Internal Network
Outgoing ICMP Traffic
NONE
Figure 9: Firewall ICMP Filtering Rules
The Internet