
intrusion_14
 ICSA, Inc.
For more information, call 888-396-8348 14
An Introduction to Intrusion Detection and Assessment
Figure 2 illustrates the existing elements of the
information security market. Intrusion detection
and vulnerability assessment fit in the sector
labeled “Assessment.”
Note that in monitoring and auditing the rest of
the products in the matrix, intrusion detection
support all of the goals.
Why Firewalls aren’t enough
A common question is how intrusion detection
complements firewalls. One way of characterizing
the difference is provided by classifying security
violation by source—whether they come from
outside the organization’s network or from within.
Firewalls act re as a barrier between corporate (inter-
nal) networks and the outside world (Internet),
and filter incoming traffic according to a security
policy.
This is a valuable function and would be sufficient
protection were it not for these facts:
1. Not all access to the Internet occurs through
the firewall.
WHERE INTRUSION DETECTION
SYSTEMS, FILE INTEGRITY AND
VULNERABILITY ASSESSMENT
PRODUCTS FIT IN NETWORK
SECURITY MANAGEMENT
Network Security Management
Network Security Management is a process in which
one establishes and maintains policies, procedures,
and practices required for protecting networked
information system assets. Intrusion Detection
and Vulnerability Assessment products provide
capabilities needed as part of sound Network
Security Management practice.
The Security Hierarchy
The following diagram outlines an Information
Security Hierarchy. It outlines the security measures
that comprise the foundation for any security
technology.
Note that in order to achieve enterprise-wide
security results, Layers 1-3 must exist in order for
the technologies and products in Layer 4 to be
effective.
Layer 4
Information Security Technologies and Products
Layer 5
Auditing, Monitoring, Investigating
Layer 3
Information Security Awareness and Training
Layer 2
Information Security Architecture and Processes
Layer 1
Information Security Policy and Standards
s
Layer 6
Validation
Source: GartnerGroup
Figure 1 - Information Security Hierarchy5
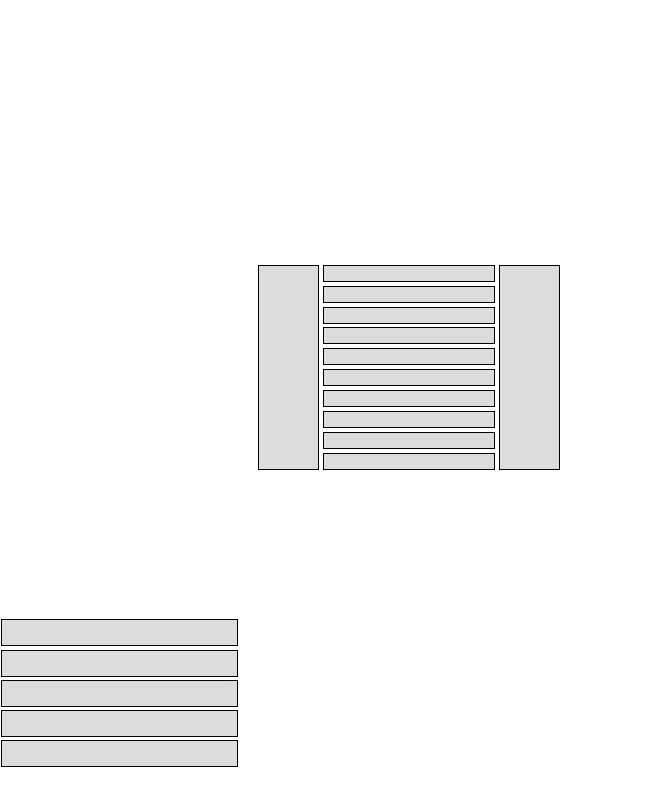
Figure 2 – Information Security Market6
Source: GartnerGroup
Firewalls
Anti-Virus
Enhanced User Authentication
Access Control and User Authentication
Cryptography
Assessment
Logging, Reporting, Alerting
Secure, Consolidated User Authentication
Certification
Physical Security
Management
&
Administration
Consulting
5 Source: Gartner Group, Conference Presentation, May, 1997.
6 Source: Gartner Group, Conference Presentation, May, 1997.
ICSA, Inc.
For more information, call 888-396-8348 14
An Introduction to Intrusion Detection and Assessment
Figure 2 illustrates the existing elements of the
information security market. Intrusion detection
and vulnerability assessment fit in the sector
labeled “Assessment.”
Note that in monitoring and auditing the rest of
the products in the matrix, intrusion detection
support all of the goals.
Why Firewalls aren’t enough
A common question is how intrusion detection
complements firewalls. One way of characterizing
the difference is provided by classifying security
violation by source—whether they come from
outside the organization’s network or from within.
Firewalls act re as a barrier between corporate (inter-
nal) networks and the outside world (Internet),
and filter incoming traffic according to a security
policy.
This is a valuable function and would be sufficient
protection were it not for these facts:
1. Not all access to the Internet occurs through
the firewall.
WHERE INTRUSION DETECTION
SYSTEMS, FILE INTEGRITY AND
VULNERABILITY ASSESSMENT
PRODUCTS FIT IN NETWORK
SECURITY MANAGEMENT
Network Security Management
Network Security Management is a process in which
one establishes and maintains policies, procedures,
and practices required for protecting networked
information system assets. Intrusion Detection
and Vulnerability Assessment products provide
capabilities needed as part of sound Network
Security Management practice.
The Security Hierarchy
The following diagram outlines an Information
Security Hierarchy. It outlines the security measures
that comprise the foundation for any security
technology.
Note that in order to achieve enterprise-wide
security results, Layers 1-3 must exist in order for
the technologies and products in Layer 4 to be
effective.
Layer 4
Information Security Technologies and Products
Layer 5
Auditing, Monitoring, Investigating
Layer 3
Information Security Awareness and Training
Layer 2
Information Security Architecture and Processes
Layer 1
Information Security Policy and Standards
s
Layer 6
Validation
Source: GartnerGroup
Figure 1 - Information Security Hierarchy5
Figure 2 – Information Security Market6
Source: GartnerGroup
Firewalls
Anti-Virus
Enhanced User Authentication
Access Control and User Authentication
Cryptography
Assessment
Logging, Reporting, Alerting
Secure, Consolidated User Authentication
Certification
Physical Security
Management
&
Administration
Consulting
5 Source: Gartner Group, Conference Presentation, May, 1997.
6 Source: Gartner Group, Conference Presentation, May, 1997.


