
intrusion_13
 ICSA, Inc.
For more information, call 888-396-8348 13
An Introduction to Intrusion Detection and Assessment
TYPE OF SYSTEM
Intrusion Detection
Vulnerability
Assessment
SYSTEM DESIGN FEATURES
Monitoring
Approach
Timing of
Analysis
Type of
Analysis
Targets and strategies
WHAT CAN IT DO?
“D” = Detects
“P” = Prevents
“R” = Repairs
“S” = Supports
Type
Examples of Security Problems
Unauthorized access to files and system resources
D
D
D
P
P
P
Violation of corporate system use policies
D D
D
D
P
P
P
Violation of corporate security policies
D D D D D
D D
P
P
Weak or nonexistent passwords
D D
D
D
D
D
Placement of trojan horses and malicious software
D P
D D D D P
P
P
Presence of trojan horses and malicious software
D
D
D D
Network service-based attacks
D D
D D
P
CGI-based attacks
D
D
D
P
P
Denial of service attacks
D D
D D
P
Failure or misconfiguration of firewalls
D
D
D
P
P
Attacks occurring over encrypted networks
D D
D
D
Unusual activity or variations from normal use patterns
D
Errors in system or network configuration
D
D
D,P,R D,P,R
Liability exposure associated with attackers using
organizational resources to attack others
P P P P P P P P P P P
P
P
Post-incident damage assessment
S S S S S S S
S
S
S
S
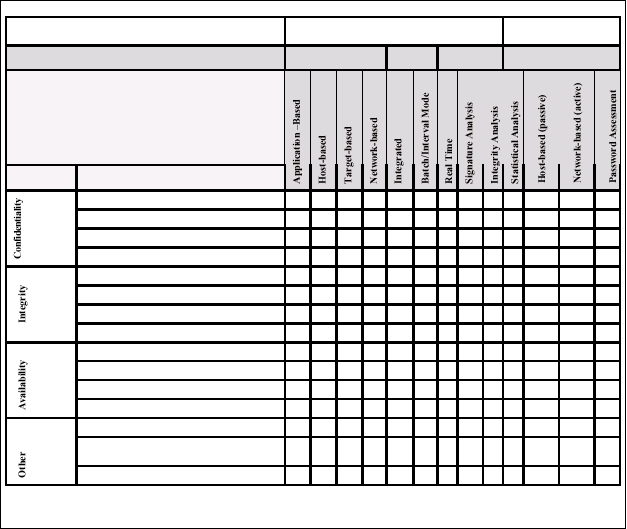
Table of Technology Features
This table outlines the features for Intrusion Detection and Vulnerability Assessment systems, outlining
the strengths and weaknesses of each. The specifics of each feature are explained in greater detail in the
Section Intrusion Detection and Vulnerability Assessment: Technical Concepts and Definitions.
Technology Features of Intrusion Detection and Vulnerability Assessment
ICSA, Inc.
For more information, call 888-396-8348 13
An Introduction to Intrusion Detection and Assessment
TYPE OF SYSTEM
Intrusion Detection
Vulnerability
Assessment
SYSTEM DESIGN FEATURES
Monitoring
Approach
Timing of
Analysis
Type of
Analysis
Targets and strategies
WHAT CAN IT DO?
“D” = Detects
“P” = Prevents
“R” = Repairs
“S” = Supports
Type
Examples of Security Problems
Unauthorized access to files and system resources
D
D
D
P
P
P
Violation of corporate system use policies
D D
D
D
P
P
P
Violation of corporate security policies
D D D D D
D D
P
P
Weak or nonexistent passwords
D D
D
D
D
D
Placement of trojan horses and malicious software
D P
D D D D P
P
P
Presence of trojan horses and malicious software
D
D
D D
Network service-based attacks
D D
D D
P
CGI-based attacks
D
D
D
P
P
Denial of service attacks
D D
D D
P
Failure or misconfiguration of firewalls
D
D
D
P
P
Attacks occurring over encrypted networks
D D
D
D
Unusual activity or variations from normal use patterns
D
Errors in system or network configuration
D
D
D,P,R D,P,R
Liability exposure associated with attackers using
organizational resources to attack others
P P P P P P P P P P P
P
P
Post-incident damage assessment
S S S S S S S
S
S
S
S
Table of Technology Features
This table outlines the features for Intrusion Detection and Vulnerability Assessment systems, outlining
the strengths and weaknesses of each. The specifics of each feature are explained in greater detail in the
Section Intrusion Detection and Vulnerability Assessment: Technical Concepts and Definitions.
Technology Features of Intrusion Detection and Vulnerability Assessment


