

|
|
The firewall industry continues to evolve rapidly as organizations demand manageable and flexible security infrastructures. For much of the past decade, firewalls have been mostly simple Internet gateway filtering devices—traffic cops that regulate flow while keeping the bad guys out. Until recently, the industry has consisted of a dizzying array of very small players competing against major system manufacturers, all of which rushed untested technologies to market to get a leg up on the competition.
After years of tumultuous change, there are signs that the firewall market is maturing. In the past year, consolidation has helped build small companies into much stronger suppliers. At the same time, large vendors have entered the marketplace with new, stable offerings and big brand names. From a technology perspective, the latest firewall solutions—from both firewall-specific vendors and large-scale systems manufacturers—are more usable and stable than previous offerings.
Merger Mania
The firewall industry (and, in a larger sense, infosec itself) is in the midst of a long-awaited period of consolidation. As recently as 18 months ago, some 70 companies offered firewall products. Following several mergers—the Axent/Raptor merger, Network Associates’ acquisition of Trusted Information Systems, and Cisco’s acquisition of Network Translation and licensing of RedCreek’s VPN technology—the firewall marketplace has coalesced around approximately 10 major players, although several minor players continue to manufacture interesting products and drive some innovation.
Is consolidation good for consumers? You bet, for several reasons. First, the support from top firewall manufacturers has improved considerably over the last year. In the past, many vendors relied on the actual software developers for customer support. While these developers were an excellent source of detailed technical information, beleaguered customers often had difficulty contacting overly busy developers.
A related benefit is that the remaining companies are more stable. In the current environment, consumers can choose from a variety of vendors without as much concern about each one’s ability to provide support, fixes and upgrades. Moreover, consolidation makes the firewall market significantly less confusing.
The downside of a marketplace with fewer competitors, of course, is the possibility that innovation and competition will suffer. However, given the thrashing, confusing marketplace of the past, a stabilized industry is a welcome change. Rapid-fire releases of difficult-to-use features have given way to a period of controlled innovation. The ultimate winners are the users themselves, who benefit from time-tested products that are less prone to vulnerabilities.
Finally, increased competition among the remaining firewall
manufacturers will ultimately lead to a reduction in unit costs.
As firewall vendors battle it out to gain dwindling market share,
many products are selling at dramatically reduced prices. For
instance, in the past, most companies had one firewall protecting
their Internet connection that cost on the order of $30,000. Today,
it’s not uncommon for a larger company to have a dozen, 50
or even 100 firewalls protecting sensitive internal networks,
multiple Internet connections and business partner access. These
firewalls may cost as little as $3,000 per unit. While this price
point still has not been reached by many of the major players,
the industry clearly is moving in that direction. Like many other
examples of the so-called "Internet economy," these
less-expensive firewalls are being bundled with more and more
features.
Packet Filters or Proxies? How ’Bout Both?
Historically, one of the great debates in the firewall industry has been which filtering technology is better: packet filters or application proxies.
Packet filters. Of the two technologies, packet filters appeared first, nearly 10 years ago. The idea behind packet filters is simple: the firewall looks through the TCP/IP header of each packet sent through it and decides whether to transmit it or not. The entire firewall operation is focused on the packet, particularly its header, which includes information such as source address, destination address, source port, destination port and direction.
In traditional packet filtering, all decisions to deny or allow packets are based on header information; no application-level information is analyzed. Because of the simplicity of their core function, packet filters tend to perform better than proxy-based firewalls. Additionally, because they sit on a connection and filter at the packet layer, they are more often than not transparent to end-users and applications.
One major limitation of packet filters, however, is their inability to understand the activities of an application. As a result, some FTP or UDP query/response services are difficult to filter. To make the process easier, some firewalls incorporate so-called "stateful" packet filters, such as Cisco Systems’ PIX, SunScreen’s SPF and Check Point’s FireWall-1. Stateful filters increase the intelligence of the filtering process by enabling the firewall to associate some new packets with packets that were previously sent through the firewall.
For example, many UDP-based applications are based on a simple query/response interaction with a server. The client software sends out a UDP request for information, and the server replies to the client with a UDP packet. These "stateful UDP" capabilities allow the firewall to remember the outgoing query. When a response is returned, the firewall verifies the source, destination addresses and ports of the response. It also correlates the response with the previous query and allows the packet to pass through. If there is no corresponding outgoing UDP query, the incoming response packet is dropped.
Proxy filters. While packet filters monitor traffic on the network and transport layers of the protocol stack, application proxy firewalls function at the application level, which gives them control over the interaction between client and server.
In the application proxy environment, a client application first connects to a process on the firewall machine that listens for client connections. This process is known as an "application proxy," a "proxy server" or simply a "proxy." After connecting to the proxy, the user is authenticated to the firewall. Next, the user (or the user’s client software) indicates which server he or she needs to access. After receiving information about the requested server, the proxy connects to the desired remote host and relays the information being sent from the server to the client (and vice-versa). At all times, the proxy application remains on the link and can limit, at the application level, what the client or server is doing.
In essence, the client software views the proxy server as the actual server. Therefore, all traffic intended for the client goes to the proxy machine rather than to the actual server. By the same token, the actual server views the proxy server as the client; all traffic at the server appears to come from the proxy server. In this way, the proxy can protect both the client and the server by authenticating the client, determining if the client can use the requested service, preventing attacks and prohibiting certain application-level events (such as FTP PUT or FTP GET).
Application proxies can also verify that the interaction between client and server actually conforms to the protocol in use (i.e., HTTP or FTP). The ability to verify the activities of the applications (rather than focus on packet headers) has been a selling point for proxy firewalls, which are marketed as having more control than packet filters and therefore more security.
Because they are more involved in the connection, proxy firewalls tend to have lower performance than packet filters. Moreover, traditional proxy firewalls required modified user methods or specialized client applications to interact with the proxy. However, most of today’s proxy firewalls—including Trusted Information Systems’ (TIS) Gauntlet, Axent’s Raptor Eagle and Secure Computing’s Sidewinder—use transparent proxy firewalls, which do not have this limitation.
Hybrid Firewalls
Packet filter or proxy, proxy or packet filter? For many years, firewall vendors have debated which technology is better. Packet filter vendors argued that their products were fast and transparent to users, as opposed to the slower proxies that required custom client software. Proxy vendors countered that their wares were more secure and flexible because the proxy could "comb" the protocol and verify that every message corresponded to it, rather than simply allowing or denying packets based on their port numbers.
Recent developments in firewall technology have rendered this debate largely obsolete. During the past year, most firewall vendors have incorporated both packet filter and proxy technologies into their products. With a so-called "hybrid" firewall, the services best handled by packet filters (such as telnet) can be packet-filtered, while those best handled by proxies (such as FTP) can be proxied. With this dual personality, firewalls can be configured to utilize the technology that makes the most sense for a given application.
Network-Level Encryption
While hybrid firewalls represent an important attitude shift about basic filtering mechanisms, they represent but one example of the trend toward building
multiple capabilities into the underlying firewall product base.
One of the most promising of these technologies is network-level encryption. Since firewalls control access to the network, they are an obvious point to place the encryption function. For instance, secure virtual private networks (VPNs) can be set up between businesses wishing to communicate across a public network. All traffic is encrypted as it leaves one firewall and decrypted when it arrives at the remote firewall.
Using VPN technology, companies can replace more costly leased communications facilities with encrypted channels across public networks, such as the Internet. Of course, potential problems—including limited Internet bandwidth and cross-organization key management—must be considered before setting up VPNs. In addition to firewall-to-firewall encryption, vendors are offering user-to-firewall VPNs in hopes of capturing some of the dialup market. With this feature, remote users simply dial up a local ISP to set up an encrypted link with the corporate firewall.
Currently, most firewall vendors support encryption between firewalls. However, many of these solutions are proprietary and do not interoperate. To address this situation, vendors have been working on a network-level encryption interoperability solution through the Internet Protocol Security (IPSec) standard, set forth by the Internet Engineering Task Force (IETF). Interoperability testing of various vendor IPSec implementations has been fostered by both RSA Data Security Inc., through its S/WAN initiative, and the automotive companies, through their creation of the Automotive Network eXchange (ANX). As a result, interoperable firewall encryption solutions should be available within a few months.
Managing the Firewall Farm
With encryption supporting firewall-to-firewall and user-to-firewall VPNs, firewall software is now being deployed enterprise-wide (see Figure 1). A few years ago, most organizations had a single firewall system. Today, firewalls are being used to support a host of activities:
Managing multiple firewalls within a single organization—a practice commonly referred to as "firewall farming"—has technological challenges of its own. While a few vendors have tackled the problem, most major product offerings do not address the issues associated with managing a complex firewall infrastructure. Many products offer the ability to log in to separate firewalls from a single management station, but this forces administrators to manage each firewall on a one-by-one basis. Frustratingly few products allow for a global view, in which a policy can be defined for a network and then deployed to all firewalls associated with that network.
Firewall Appliances
In the past year, several vendors have released so-called "firewall appliances." This term refers to several technologies, including turnkey firewall solutions, limited scope firewalls (or "not-quite-firewalls") and "do-it-all" firewalls.
Turnkey solutions. These solutions make installation easier for the consumer. Instead of obtaining the hardware, installing and hardening an operating system and installing and configuring the firewall, turnkey solutions are shipped with hardware, an operating system and a firewall already installed and partially configured. While this solution can simplify deployment, users need to verify the security of their configuration. For turnkey solutions (and any other firewall solution, for that matter), organizations should carefully check the configuration of the system and scan the firewall using a security scanning tool to ensure that no holes have been left open.
"Not-quite-firewalls." These appliances include a limited set of proxies or are devoted to protecting particular operating system platforms. For example, they may proxy only Web traffic or secure and optimize load only for Windows NT systems. An investment in this technology could be a cost-effective way of meeting current needs. However, organizations considering this solution must carefully evaluate whether they will need full firewall capabilities in the future.
"Do-it-all" appliances. These appliances involve the introduction of Internet/intranet servers onto the firewall machine itself. While many of the major players have not followed this path, a lot of smaller firewall manufactures are marketing so-called "do-it-all" appliances. In addition to traffic filtering abilities, a do-it-all firewall usually includes a Web server, a split DNS server and possibly mail and news servers—all in the same box. These appliances tend to be marketed to smaller organizations as complete Internet solutions.
While the potential for cost savings is significant, the security of do-it-all firewall bundling must be considered carefully. By placing multiple servers on a single machine, a vulnerability in any one of the servers could expose all of them (and the firewall itself) to compromises. For example, a hole in the Web server could allow an attacker to take over the system and disable all firewall filtering.
In response to these concerns, some firewall manufacturers have introduced additional security mechanisms into the underlying operating system of the firewall machine. Given the security risk, do-it-all firewalls will most likely be used in smaller organizations looking to minimize costs, or for single projects within larger companies that need quick Internet connectivity.
Here To Stay
The firewall industry has changed rapidly in recent years, both from technological and marketplace perspectives. As the market matures, consumers will benefit from a more coherent product base, more stable vendors, better support and more flexible technologies. As firewalls become thoroughly entwined in corporate networks—and as security infrastructures increasingly rely on firewalls—the trend toward stable yet flexible products represents good news to security professionals.
Edward Skoudis is a technical director at Global Integrity Corp., an SAIC company. Ed provides security consulting services on firewall architectures and technology, as well as on hacker tools and techniques. He can be reached via efs@cip.saic.com.
The Firewall Farm
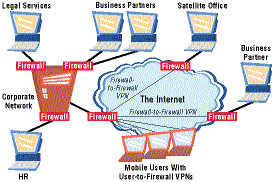
|
Figure 1 depicts the "firewall farm," in which firewalls are used to create Internet VPNs, intranet security compartments and secure business partner connections. |
|
FYI Later this year, ICSA plans to introduce version 3.0 of its firewall certification criteria. The expanded criteria, according to Firewalls Consortium Manager Pete Cafarchio, "will require vendors to provide stronger security in their default configurations, as well as improved logging capabilities." For each certified firewall product, lab notes are posted at www.icsa.net/ fpfs/fwcert.html. Updated frequently, these notes detail what intervening steps, if any, were required before a product achieved ICSA certification. |