|
|
| Black Sheep Networks takes great pride in our Government and Military designs. Our customized cross-domain solutions allow data communication from LOW to HIGH, and HIGH to LOW with various types of Gate Guard software to filter and sanitize content.
MILS and MLS architectures are our specialty. Multi Layered Security (MLS) and Multiple Independent Layers of Security (MILS) provide data isolation and controlled data downgrades and upgrades.
We have over a decade of experience with MLS and MILS designs and systems.. from traditional Trusted System designs to state-of-the-art MLS and MILS combined.. along with hypervisor technology to provide hardware virtualization. Virtualization reduces the number of physical systems required, and when running on a Trusted System it provides isolation between various classifications on the same hardware.
Government and Military consulting: |
|
Hardening Operating Systems to meet requirements
|
|
Hardening Linux, HPUX, Solaris, Trusted Solaris, VMS, IRIX, AIX, BSD, etc.. servers to meet:
STIG
DITSCAP
DCID 6/3
NISPOM
8500 Requirements
many others...
|
| |
|
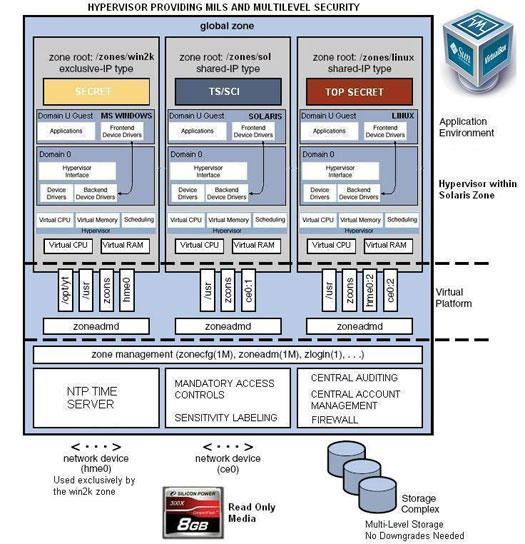
Trusted Solaris Designs and Configuration
|
Black Sheep Networks consultants are experts with Trusted Solaris 8 and Solaris 10 with Trusted Extensions. We also have extensive experience with minimizing these two platforms down to 40-50mb in size with complete Labeling, Mandatory Access Controls, and Firewall software (Zones and ZFS in Solaris 10) in order to provide the most basic functional Trusted System available. Less software = Less accreditation delays. Simplicity is the key.
|
| |
|
C&A Service
|
|
Categorization and Certification Level Recommendation
Hardware and Software Inventory
Self-Assessment
Security Awareness and Training Plan
End-User Rules of Behavior
Incident Response Plan
Security Test and Evaluation Plan
Privacy Impact Assessment
Business Risk Assessment
Business Impact Assessment
Contingency Plan
Configuration Management Plan
System Risk Assessment
System Security Plan
Security Assessment Report
Certification Test Procedures (CTP)
|

