|
 |
 |
|
|
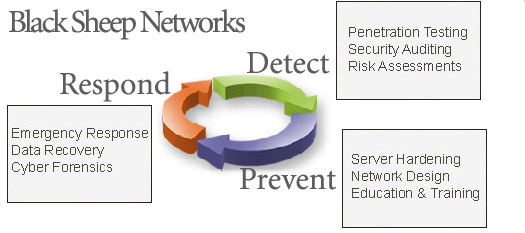
| Black Sheep Networks provides the following
Information Security consulting: |
|
Penetration Testing and Vulnerability Analysis
|
|
As a supplement to system scanning, Black Sheep engineers can effectively "hack" a target system by
breaking into it. A penetration test is a controlled simulation of an attempted intrusion against a target
site of computers to determine how robust the target site is to a hostile attack. This test mimics the
actions of a remote intruder or hacker, and attempts to bypass the target site's security and gain unauthorized
access to system data and resources.
Penetration testing is an important basic element of any security project. Without empirical testing and
best practices peer review, even the most impressive designs and implementations remain merely theoretically
secure. Only by actually testing a finished deployment can the relative security of a system be properly
measured.
Because individual needs vary, penetration testing services are custom tailored to the specific objective
of each customer. Our consultants will work with the client to properly estimate the size and scope of
the project.
Our penetration testing methodology is designed to take advantage of the creative insights of our senior
consultants through actual by-hand interactive system penetration and manual analysis of all testing
data. We do not leave critical security decisions up to programs or knowledge bases, we rely on the
experience and expertise of our in-house talent.
When necessary, our consultants create custom exploit code and attack software in order to demonstrate the
weakness of a client's network. Our personalized attention to every detail of a client's security is what
sets us apart.
In addition to manual vulnerability analysis, we also perform scans with a wide range of commercial and freely
available tools. Our vendor-neutral status allows us to use any mix of security tools as we see fit. This
gives us unparalleled flexibility, and allows our clients to make critical evaluations of the available
commercial tools in real-world tests against their own network.
Black Sheep Networks' penetration testing services can be delivered with any level of intensity that a client
desires. From completely unobtrusive network probes through full scale denial of service attack simulations,
Black Sheep Networks can deliver realistic, effective attacks which will fully exercise a client's intrusion
detection and security systems.
In addition to running tests against live, installed networks, penetration testing can also be used to evaluate
and test the security of products and services. Black Sheep will fully test pre-release products for any
possible security vulnerabilities that may be present in either the design or the implementation, and will seek
to verify and fully document any potential weaknesses that are found. Our consulting engineers will sit side
by side with your programmers and work to eliminate or mitigate any security problems that are detected. By
taking advantage of our expert critical eyes in the final stages of a client's development they can prevent
security problems before they affect their customers or their business.
We deliver our findings in the form of a comprehensive report that fully describes the testing methodology and
process we used, and documents each vulnerability fully, with solutions and recommendations presented on both a
strategic and a tactical level. We will provide full details on every potential security weakness, analyzed in
the context of your network. For each vulnerability we will discuss multiple solutions, including how to fix
the specific problem found and how to prevent it from occurring again on all relevant systems. The appendices to
our report contain actual testing output from the various security tools we used to gather our data, and
serve as an excellent baseline for comparison of future testing results. When requested, our senior consultants
are able to provide full executive briefings including demonstrations and a complete question and answer session.
Our clients have used penetration testing services on the following types of projects:
Firewall audits are an important part of ensuring a proper integration. Our consultants can empirically
verify the proper functioning of any firewall or access control device.
DMZ vulnerability testing is the only way to ensure that a busy DMZ network is free of security holes.
The many individual servers that make up web hosting farms are often upgraded and maintained in a haphazard
fashion, resulting in "configuration drift" and small vulnerabilities that creep in through software upgrades.
Pre-release security product testing is a way to ensure that the overall design of important security features
is sound. Our consultants can identify critical weaknesses, and help recommend secure deployment guidelines
and maintenance policies before your product ships to customers.
Encryption code review is an effective way to prevent errors in implementation that can critically weaken the
strength of encryption products. By having your cryptographic implementation inspected and tested by our experts,
our clients can rest assured that they have not made any mistakes that could prove fatal to the client's
security model down the road.
|
| |
|
Security Auditing
|
|
The purpose of this service is to identify risks associated with a client's network architecture and to
access the ability of the current architecture to meet the client's security needs. This is accomplished
while still meeting functionality and throughput requirements. The Security Audit is the cornerstone
for many subsequent activities as it provides an overall assessment of the enterprise and web site's security
posture.
|
| |
|
Risk Assessments
|
|
Security Assessments can be customized to include additional services such as an Internal/External vulnerability
scanning and/or penetration testing.
|
| |
|
|
|
The default installation of most operating systems is not secure. Black Sheep's host hardening
services involves a security engineer systematically walking through the installed operating system (OS)
and "locking down" or disabling specific services that are not required or have been compromised in the
past. By performing these steps, the risk of compromise for the machine will be greatly diminished.
Due to the fact that every system is unique in some way, each system has its own unique security settings that need
to be tested before implementation.
Hardening services are available for the following Operating Systems:
SUN Solaris 2.x, 8, 9, 10, 11(beta)
HP/UX 10.x, 11.x
IBM AIX 4.x, 5.x, 6.x
SGI IRIX 6.x
HP Tru64 5.x (and older Digital UNIX)
Linux (most flavors.. especially Ubuntu/Debian and RHEL3/4/5)
FreeBSD, OpenBSD, NetBSD
BSDi
Windows NT,2K,2003,XP,Vista
|
| |
|
Network Design
|
|
The best way to design security is as an integrated part of the network design and planning process.
Security that has been designed into the network from the beginning is always more effective, less intrusive,
and easier to manage over the long term. Attempting to secure a network that is already in production is
a much more complex undertaking.
This service is designed to provide high-level expertise on an as-needed basis to assist in architectural design
of large-scale security solutions. Black Sheep Networks will actively participate in planning sessions and meetings,
and will take a hands-on role in determining what security solution best fits the goals of the project. We will
suggest solutions to problems, propose workarounds to limitations, and highlight any areas of concern or
caveats.
The goal of this service is to allow a client's existing team to benefit from the expert advice of a top-notch
security consultant. Black Sheep emphasizes a team approach to consulting, in which we work together with our
customers toward a common goal. This allows a client's organization to grow and learn from our consultants, so
that they are better prepared to meet the next project.
Our clients have used this service in the past to assist with projects such as:
DNS, WINS, LDAP and other directory services play an important role in the security of the overall network.
Black Sheep Networks can help you design a system by which these services enhance security, are easier to
manage, and are more fault tolerant.
VPN deployment requires extensive planning and coordination. Black Sheep can evaluate your options and come
up with a unified plan to secure your environment with VPN technology.
PKI and cryptography planning and deployment are huge undertakings that touch on many areas of a company,
including human resources, the IT department as well as each employee. Black Sheep can plan a public key
infrastructure that supports the client's business automation as well as security needs.
Enterprise-wide firewall initiatives are the first step in bringing security to a business. Black Sheep can
evaluate solutions, provide deployment recommendations, and design an effective management and monitoring system.
E-commerce network design requires a mixture of open-access of customers, and tightly controlled security
to ensure the privacy of customer data. Black Sheep has experience securing all types of Internet connected
E-commerce networks. We understand the need to protect sensitive data (price lists, customer billing information,
inventory levels) while at the same time creating a useful site that is highly functional.
|
| |
|
Education and Training
|
|
Black Sheep offers courses and seminars that broaden our customers' knowledge of security principals,
processes, and capabilities. Current course offerings include:
Systems Security Engineering
Systems Security Planning and Policy Development
Firewall Configuration
Vulnerability Scanning Service Fundamentals
System Audit
Business Continuity and Disaster Recovery
Incident Response Fundamentals Course
Incident Response Handler's Course
|
| |
|
Emergency Response
|
|
There are many times when an immediate response to a crisis is needed. Whether it is a hacker
rampaging across corporate websites, an untraceable network problem, or an ongoing denial of service
attack, Black Sheep is ready to assist our clients in their time of need. Our consultants have the
technical depth and breadth to tackle the problems that confound our clients' staff, or simply overwhelm
them. There is no doubt that an efficient IT department is often short of manpower, and during a
crisis that shortage can mean disaster.
This service provides immediate access to network security experts in the event of a crisis. Black Sheep
Networks establishes a set of emergency contact procedures that will enable the client to summon a consultant
on short notice. Upon arrival, the Black Sheep consultant will do his utmost to resolve the problem at
hand and provide comprehensive recommendations and solutions. In addition, the consultant will work to
document the cause of the problems to the greatest extent possible.
During the crisis, our consultants will work together with the client's staff to respond to the issues
at hand. We will participate in planning meetings, take an active leadership role in addressing the situation,
and will assist in communicating with vendors and law enforcement.
Even when a client is not experiencing a crisis, Emergency Response service works for the client by providing
a quarterly network checkup and consultation. During these consultations Black Sheep will work in a proactive
role to plan and prepare for potential disasters. The client's retainer fee also ensures that our most talented
consultants are ready to go at a moment's notice, so that you'll never face a crisis alone.
Our clients are currently using this service to address the following concerns:
Hacker break-ins are becoming more common every day. Black Sheep Networks responds immediately and provides
full tracking and documentation of the incident. In addition, when the situation warrants, we have
experience working with the FBI and Secret Service to provide evidence for prosecution.
Virus outbreaks are becoming serious problems in an era when every company employee has a PC and an email account.
Worse yet, modern viruses often take advantage of application software, such as Microsoft Word and Outlook macro
viruses. Black Sheep consultants have extensive experience assisting companies during major virus outbreaks; we work
swiftly to contain and inoculate all affected areas of the enterprise.
Insider hacking and industrial espionage are becoming the most common forms of network break-ins. When
a company begins to believe it is the victim of computer crime at the hands of one of its employees, the situation is often
fraught with mistrust and uncertainty. Black Sheep can respond quickly, at the first sign of potential trouble,
to determine the facts of the matter. Our security experts are uniquely qualified to be objective investigators.
We can gather empirical evidence to determine without doubt the true facts of the matter without making our
presence known and provide expert guidance to decision makers.
|
| |
|
Data Recovery
|
|
Black Sheep can recover lost, deleted, or destroyed data. Depending on the severity, this could take quite some time in
piecing bits together for a full, or partial, recovery.
|
| |
|
Cyber Forensics
|
|
Black Sheep Networks consultants know where to look and what to look for regarding intruder
breakins or even just accidental actions that affect security or the integrity of data.
|
| |
|
General UNIX Consulting
|
|
Black Sheep Networks believes that UNIX Operating Systems, and general System Administration, are the foundation
of any Information Security consultant. A consultant cannot possibly understand what he or she is securing or
defending against if that person does not understand UNIX to the full extent. This full extent must include
UNIX based programming, application administration, and UNIX and Networking System Administration. Many of our
competitors skip this important fundamental step, which takes years of experience, and rely on under-developed security consultants
who may have no clue as to "how the engine works".
|
| |
|
Secure Dedicated Servers
|
|
Our partner, and sister company, Armored Servers provides highly secured
dedicated servers. Instead of having Black Sheep Networks design and harden your systems in-house, your company
could use our own systems instead.. accessed remotely from your office and/or home. We are also able work with your
existing IT staff and make sure your 'outsourced' servers are working properly.
| | |